Configure Ftd
In my previous post I gave you some recommendations on why use a VPN. Today I want to explain you how to configure remote access it using a Cisco Firepower Threat Defense (FTD) firewall managed by Firepower Management Center (FMC).
How to configure Remote Access VPN step by step:
Now we will see how to configure a FTD device, to allow AnyConnect connections and to use an internal Microsoft NPS server for authenticating the users.
- Windows 10 client
- Cisco virtual FTD running version 6.6.0
- Cisco FMC running version 6.6.0
Configure Licensing The FTD uses Cisco Smart Software Licensing, which lets you purchase and manage a pool of licenses centrally. When you register the chassis, the License Authority issues an ID certificate for communication between the chassis and the License Authority. In order to configure FTD failover, navigate to Devices Device Management and select Add High Availability as shown in the image. Enter the Primary Peer and the Secondary Peer and select Continue as shown in the image. I am most of the way through implementing an ASA 5508-x, controlled by a vFMC. Both are running 6.2.2.0 of the FTD and FMC software. Since the configuration is quite complex, and I would hate to have to do it all again from scratch, I figured that backing it up would be a good idea. How to configure NSEL (NetFlow) on Cisco Firepower Threat Defense (FTD) using the FlexConfig feature introduced in Firepower Management Center (FMC) software version 6.2 See the attached doc. Note that in a few versions of FTD code, the Flexconfig deployment for NetFlow as given in this document, may fail.
FMC configurations:
Create a new certificate for FTD
On the tab that will be showed please select the FTD where you want to add the certificate and who is enrolling that certificate.
In our guide we are using FMC as internal CA, that it’s a self signed certificate. We are not using a corporate CA or an external CA.
Add radius server on FMC
Add pool of addresses for VPN client

Uploading AnyConnect Images
Configure Ftd Ha
On the next menu you need to select the interface where you have to enable the SSL VPN access and which certificate you need to use for establishing VPN tunnel.
If you enable “Bypass Access Control policy for decrypted traffic” you are not able to perform any kind of filter on Access Policy from incoming VPN traffic.
Configure no NAT policy
The last step needed on FMC is to configure a new NAT policy to avoid that the traffic from the LAN to the VPN client will be natted.
Now you are able to deploy the configuration to you FTD!
We need to perform last steps on Windows NPS before to say that we have finished to configure a remote access VPN on Cisco FTD
Windows NPS configuration
Create an FTD Template
When creating a template, if you select all parts, the template will include every aspect of that device's configuration; it's management IP address, interface configurations, policy information, and so on.
If you select some of the parts, the custom template includes the following entities.
| Template Parts | Parts included in Custom Template |
|---|---|
| Access Rules | Includes access control rules and any related entities for those rules. For example, objects and interfaces (with sub-interfaces). |
| NAT Rules | Includes NAT rules and any related entities required for those NAT rules. For example, objects and interfaces (with sub-interfaces). |
| Settings | Includes system settings and any related entities required for those settings. For example, objects and interfaces (with sub-interfaces). |
| Interfaces | Includes interfaces and sub-interfaces. |
| Objects | Includes objects and any related entities required for those objects. For example, interfaces and sub-interfaces. |
Use this procedure to create an FTD template:
- In the CDO navigation bar, click Devices & Services.
- Use the filter or search field to find the FTD from which you want to create the template.
- In the Device Actions pane on the right, click Create Template.
The Name Template provides the count of each part on the device. It also shows the count of sub-interfaces, if any. - Select the parts that you want to include in the template.
- Enter a name for your template.
- Click Create Template.
- In the Parameterize Template area, you can perform the following:
- To parameterize an interface, hover (until you see curly braces) and click a cell corresponding to that interface.
- To parameterize a sub-interface, expand the interface that has a sub-interface, and hover (until you see curly braces) and click a cell corresponding to that sub-interface.
You can parameterize the following attributes to enable per-device customization.
- Logical Name
- State
- IP Address/Netmask
Note: These attributes only support one value per parameter.
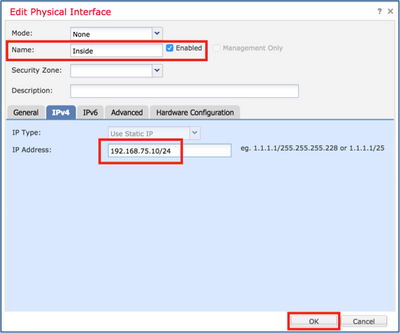
Configure Ftd Transparent Mode
- Click Continue.
- Review the template and any parameterizations. Click Done to create the template.
The Devices & Services page now displays the FTD template you just created.
Note: After creating a template, in the Devices & Services pane, CDO displays the corresponding template part icons to show the parts included in that template. This information also appears in the Device Details pane when you click the device or when you hover over the mouse pointer on the icon.
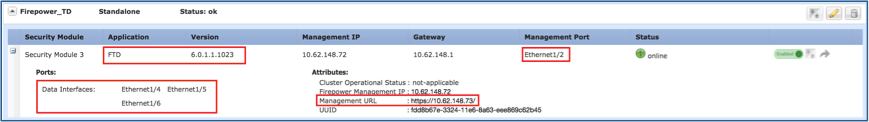
Configure Ftd High Availability
The following picture shows an example of a part icon to show that the template includes 'access rules', 'NAT rules', and 'objects'.
